 Many services offer the option to run in a so-called “chrooted” environment or chroot jail. Simply put, the service starts with a false root directory. Everything that the service requires to run is copied to the chroot directory upon startup. This would include binaries and libraries that the service requires whilst running and configuration files. Running in a false root helps protect the system from malicious attacks, the only files and directories that are available are those in the chrooted setup and they do not persist on a restart of the service. It also limits the contention to files that may occur between different services as they each have their own copy while the service is running.
Many services offer the option to run in a so-called “chrooted” environment or chroot jail. Simply put, the service starts with a false root directory. Everything that the service requires to run is copied to the chroot directory upon startup. This would include binaries and libraries that the service requires whilst running and configuration files. Running in a false root helps protect the system from malicious attacks, the only files and directories that are available are those in the chrooted setup and they do not persist on a restart of the service. It also limits the contention to files that may occur between different services as they each have their own copy while the service is running.
Each objective is available to view online. However if you prefer to have all the content in one place and study from an eBook then the objective ‘LPIC 3 Linux Security 326.1 Host Hardening’ is now available to download for just £0.99.
You also may use the command chroot when you want to recover a lost root password. Booting to a live CD and mounting your server’s root disk partition before chrooting to the partition to reset the root password. The /bin/passwd program will write to the /etc/shadow file, simple enough. However, we probably want to write to the /mnt/etc/shadow file if that is where the disk is mounted to. We would chroot to /mnt to allow this to happen. This type of chroot environment is easy to setup as all of the required files are on the existing disk partition; services have to create their own environment of startup. They will create the directory and copy all the required file resources to their correct locations in the chroot directory. In this module we will show you how to configure a simple chroot environment to run the /bin/bash and /bin/ls programs. The demonstration runs on an Ubuntu 16.04 system but is similar for any Linux distribution but the library file names may differ as may their location.
Managing Chroot Jails
Initially, we will create the chroot top-level directory. It’s name can be anything but we call it /bashjail.
$ sudo mkdir /bashjail
This directory will become the false root that we use. We know that we will need the bin directory for the ls and bash programs and an etc directory for configuration files. We will create these directories below /bashjail:
$ sudo mkdir /bashjail/{bin,etc}
We will also need one or more library directories to support the dynamic libraries used by ls and bash. We need to locate the directory names by using the ldd command for both programs we will run in the jail.
$ ldd /bin/bash /bin/ls /bin/bash: linux-vdso.so.1 => (0x00007ffc278ab000) libtinfo.so.5 => /lib/x86_64-linux-gnu/libtinfo.so.5 (0x00007f28dc3a5000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f28dc1a1000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f28dbdd6000) /lib64/ld-linux-x86-64.so.2 (0x0000564afa459000) /bin/ls: linux-vdso.so.1 => (0x00007ffdeb3ac000) libselinux.so.1 => /lib/x86_64-linux-gnu/libselinux.so.1 (0x00007f6c0a767000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f6c0a39d000) libpcre.so.3 => /lib/x86_64-linux-gnu/libpcre.so.3 (0x00007f6c0a12c000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f6c09f28000) /lib64/ld-linux-x86-64.so.2 (0x0000564646696000) libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f6c09d0b000)
From the output we will need the /lib64/ and /lib/x86_64-linux-gnu/ directories to exist within the chrooted environment.
$ sudo mkdir -p /bashjail/{lib64,lib/x86_64-linux-gnu}
The tree command is useful to display the structure we have created. If required you can install the tree program with either yum or apt:
$ sudo apt -y install tree
We can display the directories with the following command:
$ tree -d /bashjail
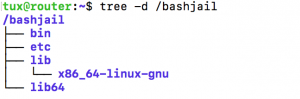
From the output, we are able to gain a better comprehension of what we mean by a chrooted environment. We emulate what we would expect at any root folder. We can get by with the minimum number of supported files and directories that are required by commands that we run from the chroot environment.
Now that we have created the directories, we will need to add the files required. First, the binaries:
$ sudo cp /bin/bash /bashjail/bin $ sudo cp /bin/ls /bashjail/bin
The central bash login script in Ubuntu is /etc/bash.bashrc in CentOS it is /etc/bashrc. We will create this file in order to customize the prompt we see whilst in the jail:
$ echo "PS1='JAIL $ '" | sudo tee /bashjail/etc/bash.bashrc
Next, we will need the library files used by the binaries. We need to copy each one to the correct directory in the jail. We can use the ldd command again if we need to remind ourselves of the files we need to copy. These files may be different on your system.
For the ls program:
$ for i in \ /lib/x86_64-linux-gnu/libselinux.so.1 /lib/x86_64-linux-gnu/libpcre.so.3 \ /lib/x86_64-linux-gnu/libdl.so.2 /lib/x86_64-linux-gnu/libpthread.so.0 ; do \ sudo cp -v $i /bashjail/lib/x86_64-linux-gnu/; done
And for bash:
$ for i in \ /lib/x86_64-linux-gnu/libtinfo.so.5 /lib/x86_64-linux-gnu/libdl.so.2 \ /lib/x86_64-linux-gnu/libc.so.6 /lib64/ld-linux-x86-64.so.2 ; do \ sudo cp -v $i /bashjail/lib/x86_64-linux-gnu/; done
Finally we have one library file in /lib64 that is shared by both programs:
$ sudo cp /lib64/ld-linux-x86-64.so.2 /bashjail/lib64/
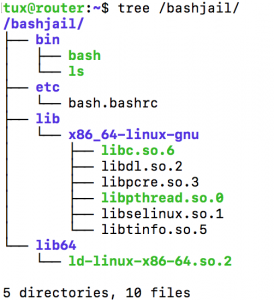
The chroot jail will now be correct and on my Ubuntu 16.04 system looks like the to the following graphic produced from the output of tree:
To execute and enter the chroot environment we need to run the command chroot with root privileges:
$ sudo chroot /bashjail /bin/bash JAIL $
We are now in the false root and we have access only to the files within /bashjail. The custom login script has executed and we see the prompt we configured. If we list the root directory we will see just the structure we created. Using the command ls -R can emulate the tree command, as we did not copy the tree command and its modules to the chrooted environment and, as such, is not available to use:
JAIL $ ls -R / /: bin etc lib lib64 /bin: bash ls /etc: bash.bashrc /lib: x86_64-linux-gnu /lib/x86_64-linux-gnu: ld-linux-x86-64.so.2 libdl.so.2 libpthread.so.0 libtinfo.so.5 libc.so.6 libpcre.so.3 libselinux.so.1 /lib64: ld-linux-x86-64.so.2
We are restricted to just these files and nothing else. To leave the chroot environment we just type exit. The command exit is a shell builtin so is always available to bash.
